Is The Seatbelt Fastened On Your Cloud Services?
Getting to your destination safely with private, public, or hybrid cloud services.
By Scott Montgomery, vice president and chief technical strategist, Intel Security
The key to securing and managing cloud applications is not simply which technology is being used; it is having a clear understanding of who is responsible for each component of security and ensuring there are no gaps, no seatbelts left off.
Cars are very secure; they have seat belts, air bags, crumple zones, and an increasing range of features to help the driver detect and avoid collisions. However, tens of thousands of people are killed or injured every year in cars because they didn’t do up their seat belt, and many others affected by unsafe driving.
Cloud services, whether we are talking about software, infrastructure, or platform as a service, are cost effective, highly flexible, and very secure. But you have to use the available security features appropriately and augment them as necessary, as you would with a child’s car seat. Without this extra step, your data is riding in a car at high speed without a seatbelt.
Each of the major cloud service providers delivers their services at different layers. For example, if you are running SQL server on Amazon virtual machines, you are responsible for making sure your SQL code is up to date on its patches, while Amazon keeps the underlying operating system current. Getting breached through a known SQL vulnerability is not a failure of cloud security.
If you are sharing documents via Dropbox, you are responsible for local storage while they encrypt the transmission and the remote storage. Using a weak password or leaving the data on your endpoints unencrypted is not a failure of cloud security. Perhaps more important, who is responsible for storing, maintaining, and providing access to the encryption keys?
Security gaps between the provider and the owner have been at fault for many of the cloud security breaches we have seen so far. Since finger pointing will not get your data back, it is critical to understand who is doing what as well as how you will measure success for what they are doing before moving to the cloud. And assume that, if you do not know exactly who is responsible for a specific task, it means no one is doing it.
Based on our recent study of cloud security, organizations are using an average of 30 cloud services IT knows about and another 12 they have no visibility and control over. These are spread across a slowly consolidating but still broad set of providers and could be software, infrastructure, or platform services. Almost 25 percent of the 1,400 IT professionals surveyed have experienced data loss with a cloud service provider, and more than 50 percent have tracked malware infections back to a cloud application.
Securing this range of services means starting with the security SLAs from each provider and identifying exactly where the lines of responsibility are and what responsibilities are shared. Cloud providers are generally delivering excellent security for their services, but only for their portion. This chart summarizes where the typical lines of responsibility are drawn for the different types of cloud services and should serve as a useful and frequent reminder.
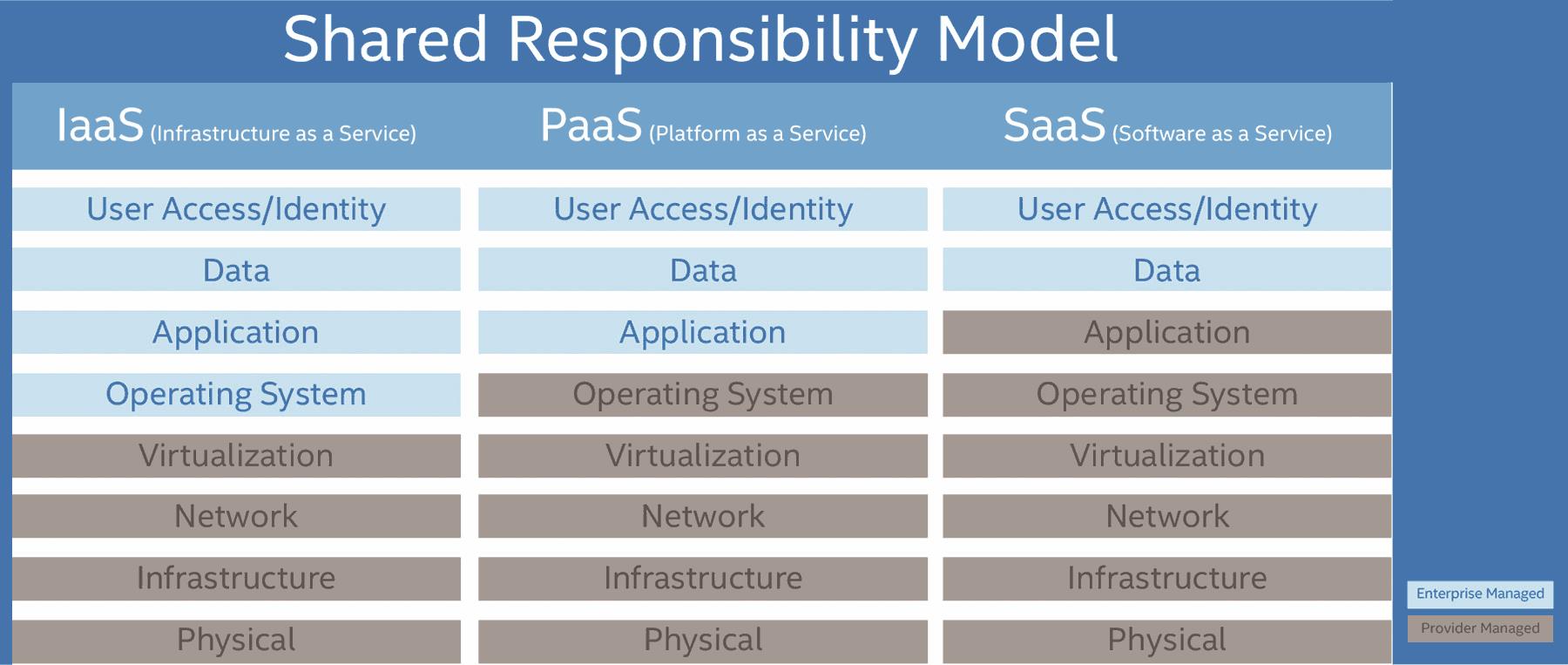
User access and identity is always the responsibility of the customer and should be protected with strong and unique passwords, as well as multi-factor authentication. Admin accounts are especially valuable targets and they should also have multi-factor authentication or biometric security enabled, and there should be no administrative sharing of root or super-user credentials. This may seem obvious, but stolen or hacked account credentials remain the number one attack vector, often benefiting from reused passwords stolen from less-secure sites.
Data protection is also the customer’s responsibility. Encryption is an excellent foundation for securing your data as it is independent of the type of cloud service. Data can be classified and policies enforced with centralized data loss prevention tools, making it seamless and transparent to users. This type of security offers protection against data loss from accidental insider actions to sophisticated attack campaigns, when properly implemented.
These two security practices are the seatbelt and airbags of cloud security; they protect the majority of users from the majority of risks with minimal effort. Many additional layers of protection are available, depending on the type of cloud service and desired risk profile, but they will only protect you if you turn them on, do them up, and drive defensively.
